CCBD Expo Insights
Explore the latest trends and innovations in the CBD industry.
Secure and Decentralized: The Match Made in Data Heaven
Discover how the perfect blend of security and decentralization transforms your data management. Unlock the future of data today!
Exploring the Synergy Between Security and Decentralization in Data Management
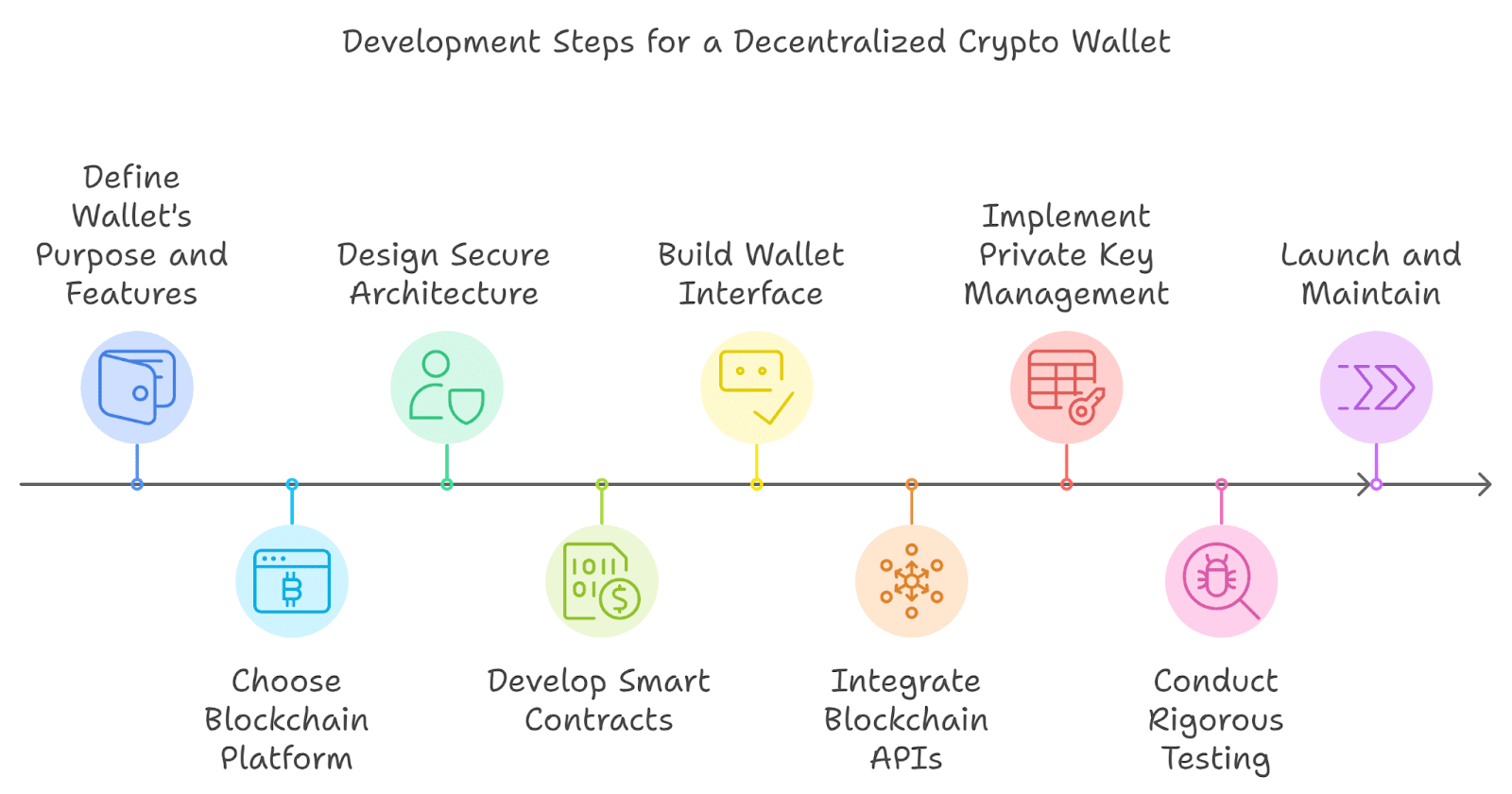
In today's rapidly evolving digital landscape, organizations are increasingly recognizing the importance of combining security and decentralization in their data management strategies. This synergy not only enhances the protection of sensitive information but also fosters greater resilience against potential threats. By utilizing decentralized systems, businesses can eliminate single points of failure, making it significantly more challenging for malicious actors to compromise data integrity. Moreover, decentralized architectures empower users by granting them greater control over their data, reinforcing trust in the system.
The integration of security and decentralization enables a more robust framework for data management through various methods. For instance, employing technologies such as blockchain facilitates transparent data transactions while ensuring that all activity is immutable. These attributes not only strengthen security measures but also enhance accountability. Additionally, organizations that embrace this dual approach can streamline compliance with regulatory standards, safeguarding their operations while remaining agile in a dynamic market. As businesses continue to navigate the complexities of data management, the interplay between security and decentralization will be pivotal in shaping a secure digital future.
Counter-Strike is a popular multiplayer first-person shooter that emphasizes teamwork and strategy. Players can choose to join either the Terrorist or Counter-Terrorist teams, engaging in various game modes such as bomb defusal and hostage rescue. You can enhance your gaming experience with exciting offers like the cryptocasino.com promo code, which provides great bonuses for players looking to dive deeper into the game's competitive scene.
How Decentralized Systems Enhance Data Security: A Comprehensive Guide
Decentralized systems are revolutionizing the way we approach data security. Unlike traditional centralized models where a single point of failure can compromise the integrity of data, decentralized architectures distribute information across multiple nodes. This distribution not only reduces the risk of hacking but also enhances data security through redundancy. In a decentralized system, even if one node is attacked, the remaining nodes continue to operate, ensuring that data remains intact and accessible. This characteristic is particularly vital for industries handling sensitive information, such as finance and healthcare, where data integrity is paramount.
Furthermore, decentralized systems often leverage advanced cryptographic techniques to secure data during transmission and storage. These systems can utilize mechanisms like blockchain technology, which adds an additional layer of security through immutability and transparency. Each transaction is recorded in a way that once validated, cannot be altered or deleted, significantly enhancing data security. As organizations continue to prioritize data security in an era of increasing cyber threats, understanding the advantages of decentralized systems becomes essential for safeguarding sensitive information and maintaining user trust.
Is Decentralization the Key to Secure Data Storage?
As we dive into the age of digital transformation, the question arises: Is decentralization the key to secure data storage? Traditional centralized data storage systems are often vulnerable to a single point of failure, making them attractive targets for cyber attacks. In contrast, decentralized systems distribute data across multiple nodes, enhancing security through redundancy and minimizing the risk of data loss or corruption. Many experts believe that implementing decentralized data storage solutions can significantly bolster security protocols, making it much more difficult for malicious actors to compromise large amounts of data.
Additionally, the decentralization of data storage aligns seamlessly with the principles of blockchain technology, offering transparency and traceability. In decentralized networks, every participant has access to the same data, which promotes integrity and trust among users. As organizations face increasing scrutiny over data privacy and security, adopting decentralized methods can empower them to maintain control over their data while ensuring compliance with regulations. Ultimately, embracing decentralization not only enhances security but also paves the way for innovative approaches to managing sensitive information in today’s interconnected world.